JensenIT Blog
Cybersecurity is intensely important, so a business owner would think implementing every security feature and defense would be a good idea. However, as research has shown, this can be counterproductive, as only 67% of surveyed security leaders know what led to cybersecurity incidents in their businesses over the past year.
The world’s largest ticket retailer is in hot water after their parent company, Live Nation Entertainment filed an 8-K filing with the Security and Exchange commission admitting that they had been hacked to the tune of 1.3 terabytes of information. That amounts to 560 million customers’ personal information that has been stolen from the company’s servers. Today, we take a look at the hack and what it means for consumers.
Mobile malware isn’t common, but it’s growing increasingly more so. You may have heard of a malware called XLoader, which has been used to victimize people in over seven countries. This mobile threat has seen various iterations over the past several years, but you should be especially concerned these days.
If you are old enough to remember when antivirus (like most computer software) came in a great big textbook-sized box at the store, then you probably remember a time when that was the only protection you really needed.
Today, there are countless free versions of antivirus out there. Let’s talk about how much protection these actually bring, and when and where they might be a good fit.
We’re hoping that you are actually reading this post to prepare yourself if your business were to face a ransomware attack, but if you are suffering from one right now, we encourage you to reach out to us immediately, whether you are a client or not. Ransomware spreads quickly, and once it has infected a system, there really isn’t much you can do to stop it. However, there are steps you need to take to come back from this gracefully.
With technology being an integral part of our lives and society at large, cyberthreats continue to evolve and pose significant risks. One such threat that is on the rise is browser hijacking attacks. Let’s explore the dangers of these attacks, including the techniques employed by hackers, and how small and medium-sized businesses can protect themselves.
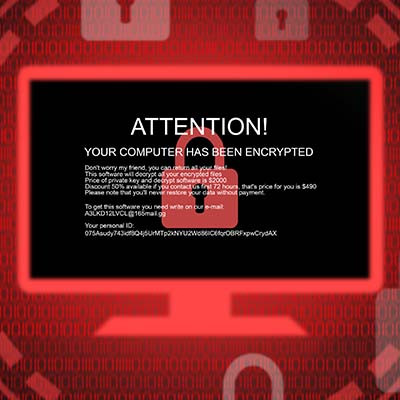
Ransomware is one of the worst situations that any business could have to deal with. It not only holds your data or computing infrastructure for ransom, it also creates situations where you have to explain to your clientele that you’ve been breached and that their information has fallen into the hands of scammers looking to extort your business. This month, we thought we would take you through a ransomware attack to give you an idea of just how unpleasant it is.
Even if mobile malware doesn’t have nearly as much of a presence in the cyber threat landscape as other major threats like ransomware variants, it is still just as dangerous under the right circumstances. An Android banking malware called Sova, for example, has returned with a vengeance with additional features to make users’ lives miserable.
As a business professional, it’s your responsibility to protect your company’s digital assets from cybercrime, but the path forward is not always so easy or clear-cut. Without a thorough knowledge and expertise of IT security at your disposal, it can be challenging to protect your infrastructure as adequately as it needs to be. Here are some of the common issues that involve cybersecurity, as well as how you can address them.
Network security could mean any number of things, but more often than not, people are using the term as a blanket statement against the dreaded idea of malware and its many forms. Today, we are discussing how vast the world of malware can be and how often you might find yourself misunderstanding what it exactly is. Knowing all this can help you identify if you have become a malware victim or not.
Ransomware is widely regarded as one of the worst modern cyberthreats out there today, and there's plenty of evidence to support this. These attacks and their aftereffects can devastate businesses of all industries. Let's consider why it is that ransomware is so dangerous, and what can be done to fight it.
Many threats immediately make themselves known on your device the second they install themselves, like ransomware and other types of malware. Others, like this newly discovered threat called MosaicLoader, discreetly install themselves in the background of your device and cause problems behind the scenes.
You often hear about malware that infects desktop PCs, laptops, or servers, but other types of malware that infect mobile devices also exist. One such malware, a threat called TangleBot, has been discovered, and it can become seriously problematic for both workers and consumers utilizing Android devices—especially in today’s mobile-centric workplace.
The cyberattack on SolarWinds was devastating for many reasons, and Microsoft has officially uncovered yet another type of malware used in the attack on the software provider. This time, it is a backdoor threat they have named FoggyWeb. What does this threat do and why is it so important to look at this incident even now?
While it only makes sense to assume that a cybercriminal would focus specifically on those targets that would bring them the greatest profit—in other words, larger businesses—the reality of modern cybercrime renders this assumption grossly outdated. Let’s examine how different developments in ransomware have made it possible for cybercriminals to be far less discerning in who they target.
Ransomware is such a massive threat that all businesses should be aware of the latest news and findings regarding how it spreads and how it can be prevented. According to a recent report, the latest modes of transporting ransomware have been revealed. What can your organization do to keep ransomware off of its network? Let’s find out.